Tunneling Through a SOCKS Proxy
Lesson Overview
During your career as a Web Application Penetration Tester you will no doubt come across a scenario where you need to test an internal non-production application for one of your clients. Certainly the easiest way to go about doing this would be to hop on an airplane and fly to one of their corporate offices to perform the testing on their LAN. This is however also the most expensive option and often the least preferable one. This video will explain how to connect Burp Suite to a SOCKS proxy server which you have created via an SSH tunnel to your clients internal LAN in order to test the non-production application from the comfort of your home or office.
Action Steps
First we create an ssh tunnel specifying the SOCKS proxy port with the -D option.
:~$ ssh user@server_name_or_ip_address -D 4321
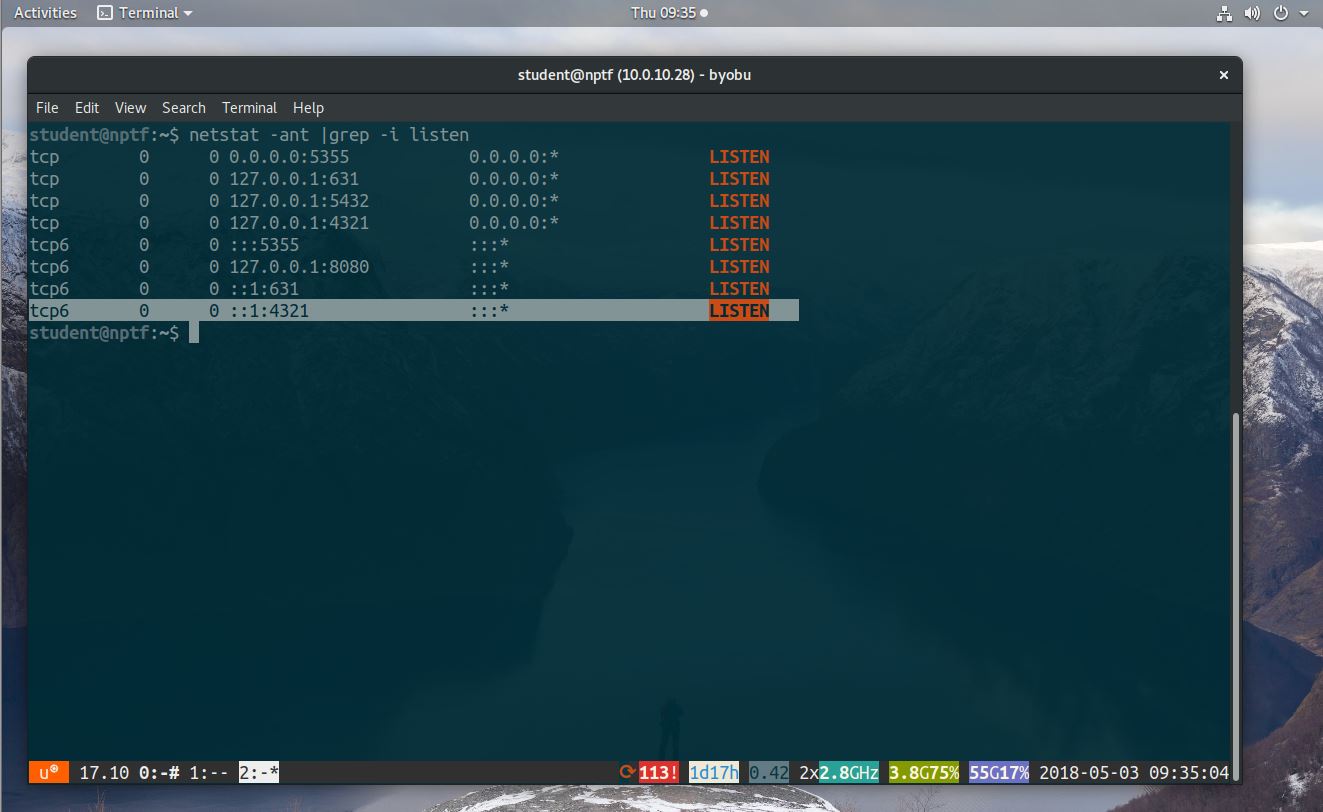
We can use netstat to verify that the port we specified is listening on our attacking system.
:~$ netstat -ant |grep -i listen
Next we tell Burp Suite to use our SOCKS proxy by specifying the IP address and port number in the user options tab. Make sure to check the box to use the SOCKS proxy and also to perform DNS lookups through the proxy.
Host: 127.0.0.1 Port: 4321
Finally, configure your browser’s proxy settings to route through the Burp HTTP proxy on port 8080. If you’ve done everything correctly, you should be able to access your target application and intercept traffic with Burp.